Cryptocurrency is all the rage right now. With amateurs getting in on the hype to learn how to trade it and watching the market escalate day to day, it can be a very exciting endeavor. But what happens when those with huge social media accounts, including Elon Musk and even Mr. Bitcoin himself, are hacked and then advertising bitcoin scams on their platforms? Absolute mayhem, that’s what.
This exact circumstance became Twitter’s worst nightmare last July, and for good reason. Approximately 130 accounts were affected and 45 were actually used to tweet scam messages, and most of the accounts that were accessed in the scam had at least a million followers. The scammers are believed to have received about 400 payments in bitcoin valued at $120,000.
The real kicker is, the “hacker” was not a professional by any means. In fact, he was just shy of becoming a legal adult – which is lucky for him and his impending jail sentence. All of this is to say that it does not take a professional team of adult hackers to take down not only one of the largest social media platforms in the world, but also some of the most influential politicians and celebrities, who we hope would have higher security than us regular civilians.
So, let’s break down the hack to understand how this happened, and talk about how businesses can put measures in their security strategy to ensure it does not happen to them. This “elaborate” plan – put in quotes because while it was elaborate in that it was successful, it was also not difficult at all for this teen to execute it because it was a social engineering scam that happens so often. Social engineering is essentially an attack where the victims are tricked into providing confidential information through very convincing scams.
An example of what the posting on Twitter looked like is below, and as you can see, it came from our former president, Mr. Barack Obama. So you can only imagine how influential and real it felt for the average Twitter user who happened to be scrolling through and is already excited around the hysteria of bitcoin.
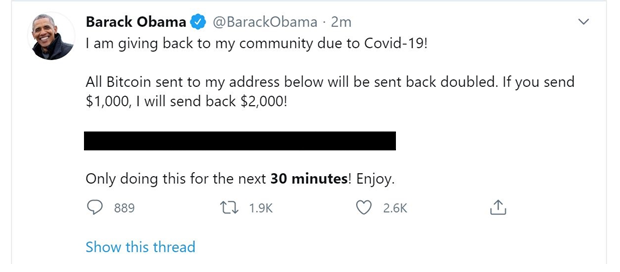
Some of the other high profile accounts included Jeff Bezos, Michael Bloomberg, Joe Biden, Bill Gates, Kanye West, Wiz Khalifa, Elon Musk and Kim Kardashian. All 130 of the accounts that were compromised were to promote the same bitcoin scam. The tweets were flying in at such a rapid rate the bitcoin hashtag went viral, again making it seem as though it was even more real than it was.


In this case, the attacker gained access to the admin tools that Twitter was using in order to recover and reset accounts. Think about when you forget your password on any site – an email is sent to the admin of the site, and a reset password code is sent to your email. That tool at Twitter was the main victim of this crime, because the hacker was then able to go into the most prestigious accounts and change their passwords so he could take full control of what they posted.
But how did he get that far? Well, there could have been a few vulnerabilities at play that gave him the advantage of getting in. Because so many employees were working remotely, some of them were allowed to run internal admin functions from their locations, which were likely not to be the most protected of places. And for many of these employees, they could have been permitted to even run these functions on their own devices, which without the proper security in place, could mean a multitude of vulnerable access points.
According to the Information Systems Audit and Control Association (ISACA), the process by which this teenage mastermind achieved inner access could have been by:
While we may not feel pity for Twitter because of their massive presence, any business is just as susceptible to a social engineering hack of this kind. Imagine a small-to-medium-sized business, where employees wear multiple hats and everyone is working their hardest. A person in accounts payable could receive a very convincing email about a wire transfer that appears to come directly from their CEO, which isn’t uncommon in a smaller sized company. Since it appears real, and this employee has a lot on their plate, they proceed with the transfer and within minutes the hackers are in. This has significant implications to the business’ data.
How can any business, regardless of their size, ensure that this will not happen to them?
An end-to-end security approach is a great place to start when it comes to protecting your business. This way, every “end,” or vulnerable place where a hacker could potentially get in is protected.
Security Awareness Training is a great way to educate employees to be on the lookout for phishing emails or anything suspicious for that matter. Security Monitoring ensures that your business is being watched 24/7, 365 days a year, and will make you aware of anything potentially hazardous to your data. And Vulnerability Management is ideal to classify and potentially remediate any threats. Lastly, any access point in your office can create vulnerability, but with MFP protection, you have another added layer of security. No matter what your security needs are, document and data protection, video security, or cyber security, this all-encompassing blueprint was designed to ensure you have security today for stability tomorrow. 😉